In today’s digital age, data privacy and security have become paramount concerns. With the increasing possibilities of data breaches and unauthorized access, it is critical to employ effective measures to protect sensitive information. One such tool that has gained popularity is Shreddit. In this blog post, we will explore what Shreddit is, how it works, and its significance in safeguarding your data.
What is Shreddit?
Shreddit is a Python package that offers a convenient way to securely delete files and directories from your computer. It uses various secure deletion algorithms to overwrite the content of the files, making the data unrecoverable. Shreddit can be used to protect sensitive information and maintain better privacy by ensuring that deleted files cannot be recovered by unauthorized individuals. It is commonly used by individuals who have concerns about data privacy and want to ensure that their deleted files cannot be recovered.
How does Shreddit work?
Shreddit works by securely deleting files and directories from your computer using specific secure deletion algorithms. Here is a high-level overview of how Shreddit typically functions:
1. Selection of Files/Directories: You provide Shreddit with the files or directories you want to delete securely. This can be done through command-line arguments or by specifying paths programmatically.
2. Algorithm Selection: Shreddit allows you to choose the secure deletion algorithm you want to use. You can select from various algorithms like Zero-Write, Random-Data, Gutmann Method, DoD Method, etc.
3. Overwriting Process: Once the files or directories are identified, Shreddit begins the overwriting process. It reads the file content and overwrites it with the chosen algorithm, making the original data irrecoverable. Depending on the selected algorithm, Shreddit may perform multiple passes to thoroughly erase the data.
4. Verification: After the overwriting process, Shreddit may optionally verify the successful deletion by comparing the file’s size or content with the original data.
5. Deletion Confirmation: Once the files have been securely overwritten, Shreddit may prompt for confirmation before proceeding with the deletion. This is to ensure that you intend to delete the files and to prevent accidental deletions.
6. Permanent Deletion: Upon confirmation, Shreddit proceeds to permanently delete the files from your computer. It uses standard file deletion methods provided by the operating system, ensuring that the overwritten data cannot be recovered by normal means.
7. Logging and Reporting: Shreddit may keep a log of the files and directories it deletes, along with any relevant information such as file sizes, deletion timestamps, and the chosen secure deletion algorithm. This log can be helpful for auditing purposes or to track the deletion activities.
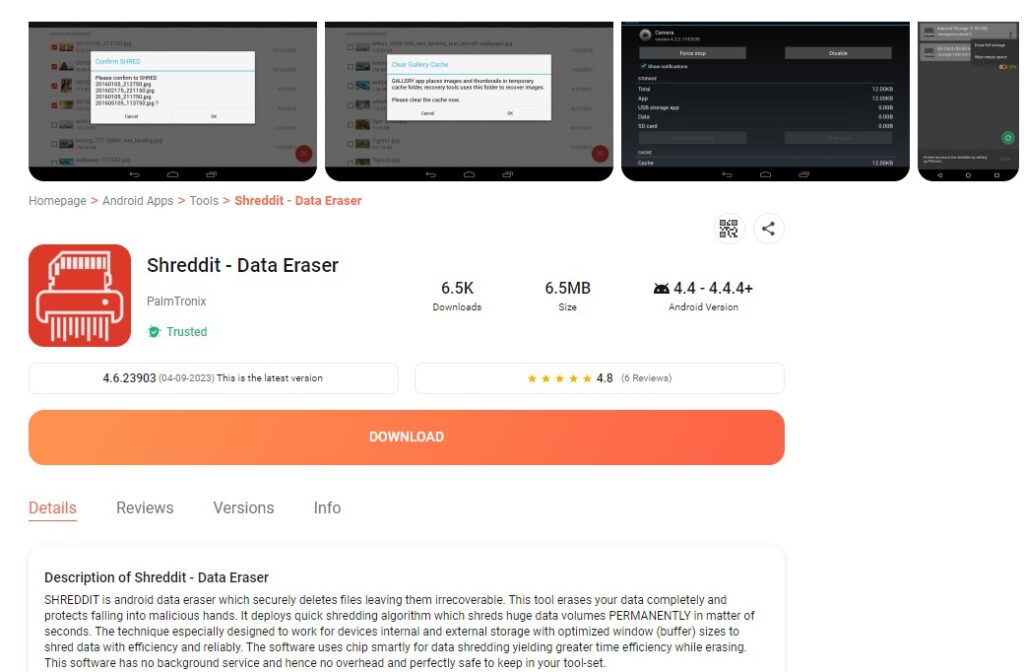
It’s important to note that Shreddit is a powerful tool for securely deleting files, but like any software, it has limitations. It cannot guarantee data deletion on devices that have advanced data recovery techniques or in cases where other copies of the data exist outside the specific files or directories being deleted. Therefore, it is always advised to use Shreddit as part of a broader data security strategy and exercise caution when handling sensitive information.
What are some secure deletion algorithms used by Shreddit?
Shreddit utilizes various secure deletion algorithms to ensure the data is irrecoverable. Some of the commonly used algorithms in Shreddit are:
- Zero-Write (Zero-Fill): This algorithm overwrites the file contents with zeros, effectively erasing the original data.
- Random Data: This algorithm replaces the file content with random data, making it difficult to recover the original information.
- Gutmann Method: The Gutmann Method is a multi-pass algorithm that overwrites the file content multiple times with specific patterns. It is designed to provide greater security by ensuring thorough data destruction.
- DoD Method (Department of Defense): The DoD method is a data sanitization algorithm recommended by the United States Department of Defense. It involves multiple writes of specific bit patterns performed in a sequence to securely erase the file.
These algorithms, along with others used by Shreddit, are designed to provide a higher level of security when deleting files, making the data unrecoverable by standard recovery methods.
Key Benefits of Shreddit
Shreddit offers several key benefits for securely deleting files and directories:
- Data Privacy
Shreddit helps protect your sensitive information by securely deleting it from your computer. By using secure deletion algorithms, Shreddit ensures that the deleted files cannot be easily recovered, maintaining your data privacy.
- Permanent Data Removal
Shreddit performs thorough data overwriting, making the original data irrecoverable. It goes beyond traditional file deletion methods, reducing the risk of data breaches or unauthorized access to deleted files.
- Multiple Secure Deletion Algorithms
Shreddit provides various secure deletion algorithms to choose from, allowing you to customize the level of data destruction based on your security needs. Algorithms like Gutmann, DoD Method, and Zero-Write offer different levels of security for file deletion.
- Ease of Use
Shreddit is designed to be user-friendly, making it accessible even for users with limited technical knowledge. It can be easily executed from the command line or integrated into other software applications as part of automated processes.
- Auditing and Tracking
Shreddit keeps a log of the files and directories it deletes, providing a record of the secure deletion activities. This can be valuable for auditing purposes or to track the deletion history for compliance or security reviews.
- Open-Source and Community-Driven
Shreddit is an open-source project, which means its code is freely available for review and collaboration. This encourages transparency, security audits, and improvements by the community, enhancing the reliability of the software.
It’s worth noting that while Shreddit is a useful tool for secure file deletion, it is always important to handle sensitive data with care and follow best practices for data security to ensure comprehensive protection.
Can I use Shreddit for iOS?
Shreddit is primarily a Python package designed for use on desktop operating systems like Windows, macOS, and Linux. As such, it may not be directly compatible or available for use on iOS devices.
However, there are alternative applications and methods available on iOS that can help you securely delete files and maintain data privacy. Here are a few options you can consider:
- Built-in Data Erasure
iOS devices have built-in features for securely erasing content. This can be accessed by going to “Settings” > “General” > “Reset” > “Erase All Content and Settings”. Keep in mind that this process will erase all data on the device, so be sure to have any necessary backups in place.
- Third-Party Apps
There are several third-party apps available on the App Store that offer secure deletion capabilities for iOS devices. These apps often implement various secure deletion algorithms and provide user-friendly interfaces for securely deleting files and data.
- Cloud Storage
If you use cloud storage services like iCloud, Dropbox, or Google Drive on your iOS device, these services often provide the option to securely delete files from their servers. You can explore the settings and options within these cloud storage apps to securely manage and delete your files.
In conclusion
Shreddit provides a reliable solution for securely deleting files and directories from your computer. With its secure deletion algorithms and user-friendly interface, it offers a convenient way to safeguard your data and maintain privacy. By overwriting file contents using methods like Zero-Write, Gutmann Method, and DoD Method, Shreddit ensures that the original data becomes irrecoverable, reducing the risk of unauthorized access or data breaches.

![How to Pause Location on Find My iPhone Without Them Knowing? [2024] 20 how to pause location on find my iphone](https://izood.net/wp-content/uploads/2024/10/How-to-Pause-Location-on-Find-My-iPhone-Without-Them-Knowing-400x300.png)

![How To Inspect Element on iPhone [4 Methods] 23 how to inspect element on iphone](https://izood.net/wp-content/uploads/2024/10/how-to-inspect-element-on-iphone-3-400x300.png)